Qlik Data Gateway - Direct Access
Businesses commonly enforce strict firewall policies that block external access to their data sources. This presents a challenge when such businesses need to access their data from the cloud for analytics. Qlik Data Gateway - Direct Access overcomes this challenge by eliminating the need to open inbound firewall ports. Operating behind your organization’s firewall, the Direct Access gateway allows Qlik Sense SaaS applications to securely access behind-the-firewall data, over a strictly outbound, encrypted, and mutually authenticated connection.
Qlik Data Gateway - Direct Access architecture
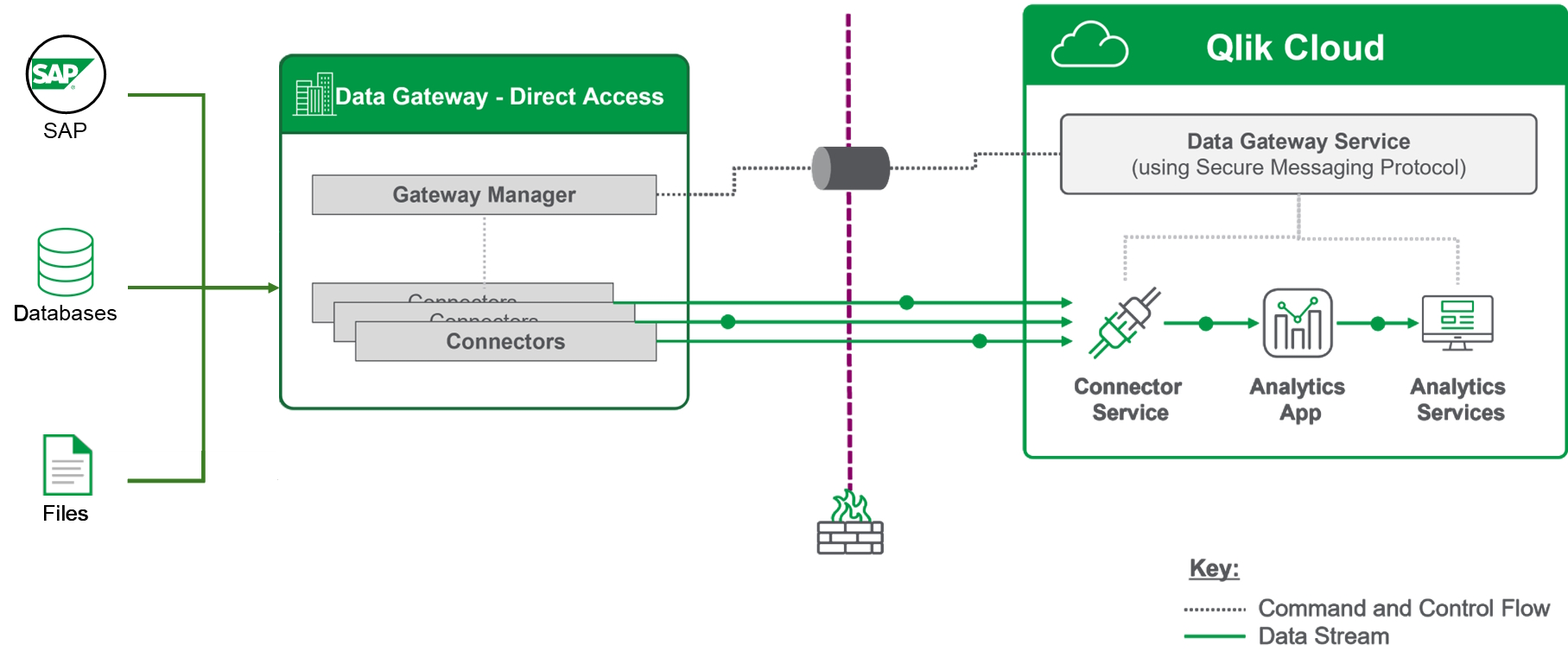
The high-level communication sequence is as follows:
-
The Direct Access gateway establishes a mutually authenticated and encrypted connection to Qlik Cloud, using HTTPS.
-
Qlik Cloud sends a load statement (query) to the Direct Access gateway.
-
The Direct Access gateway relays the query to the relevant data source.
-
The data is then pushed (streamed) directly from the data source to Qlik Cloud over WSS.
