Roles and permissions for users and administrators
Users’ permitted actions in Qlik Cloud are determined by their roles. A role is a set of permissions that can be assigned to individuals or groups of users. By assigning roles, you can better organize your users and what they can do in the tenant. The roles can be changed at any time. Anonymous users received limited permissions to view publicly shared app
This topic is applicable to Qlik Anonymous Access subscriptions. For other Qlik Cloud subscriptions, see:
-
Standard, Premium, or Enterprise edition of Qlik Cloud Analytics or Qlik Cloud Data Integration: Managing users - Capacity-based subscriptions
-
Qlik Sense Enterprise SaaS, Qlik Sense Business, or Qlik Cloud Government: Managing users - User-based subscriptions
Access control in Qlik Cloud is divided between tenant-wide roles and space roles. Understanding how they interact is essential for effectively managing user access. Tenant-wide roles authorize actions across the entire tenant, and space roles grant access to content in specific spaces. The roles on tenant level include built-in security roles and custom roles created by administrators. Additionally, all users have a set of universally applied default permissions.
Security roles
Security roles provide access to different capabilities in Qlik Cloud. Security roles are divided into administrator roles and user roles.
-
Administrator roles enable management of tenant-wide functions that affect governance, performance, and security.
-
User roles enable access to features in the tenant and actions on resources, such as creating spaces or accessing personal content.
For more information about the permissions granted with each role, see Permissions granted by security roles.
User default permissions
The User Default settings grant basic permissions to all users in the tenant. The role can't be unassigned or deleted, but administrators can modify the permissions. The default permissions decide what users can do in Qlik Cloud before any other roles are assigned.
Tenant administrators need to decide what permissions everyone should have and assign additional permissions based on users' work requirements through roles. As a best practice, follow these steps to ensure secure access control for specific features:
-
Create a custom role tailored to users who require access to the feature, assigning them appropriate permissions.
-
Adjust the User Default permissions by removing default access to the feature, thereby preventing unintended users from accessing it.
This approach ensures users have the right permissions to do their job without granting unnecessary access, and reduces disruptions for users who need to use the feature.
Editing user default permissions
Tenant administrators can edit the permission levels in the User Default settings.
Do the following:
-
In the Administration activity center, go to Manage users > Permissions.
-
Click User Default above the table.
-
Add or remove permissions as needed.
Tip noteYou can use the List all and Selected buttons to show all available permissions or only the selected ones. -
Save the changes.
Information note Users must log out and log in again for the changes to be applied.
The permission configuration options are described in Permissions in User Default and custom roles.
Custom roles
Custom roles give administrators the flexibility to define roles tailored to specific needs, for example access to capabilities where special knowledge is required or where capacity is limited. These roles complement the built-in security roles, providing additional granularity in managing permissions on both tenant level and individual level.
Custom roles extend permissions beyond those granted by the User Default settings. When assigning a custom role to users, permissions can only be added, not removed.
For more information on how to create custom roles, see Managing custom roles.
Space roles
Space roles determine what a user can do with the content in a specific space. Spaces are sections of Qlik Cloud used to collaboratively develop and control access to resources such as apps or automations. The roles are defined at the space level and apply only to content within that space.
For more information on space roles, see:
How user default permissions interact with custom roles
Custom roles add permissions beyond those allowed by the user default, but can't revoke permissions. It's important to note that attempting to restrict a permission that is allowed in the User Default settings will have no effect. The permission will still be allowed to everyone.
The table shows the permission levels that can be granted by a custom role, depending on the corresponding value in the User Default settings. You can also choose to inherit the User Default permission, shown as "User default (permission setting)". This means that the setting in the custom role will match whatever the default is set to.
| Configured User Default permission level | Possible custom role permission level |
|---|---|
| Allowed | Allowed |
| Not allowed | Any available permission level |
| Other permission levels | The same or a higher permission level |
For details on the permission levels, see Permissions in User Default and custom roles.
As an example, consider a scenario where the User Default automatically grants a specific permission to all users. When creating a custom role, this permission appears as "User default (Allowed)" and doesn’t need explicit configuration as it’s already allowed by the User Default.
The permission is automatically allowed for all users via the User Default.
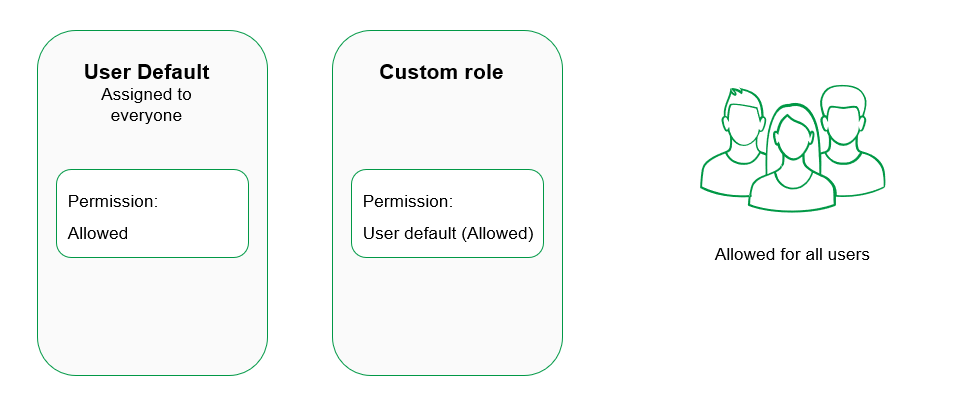
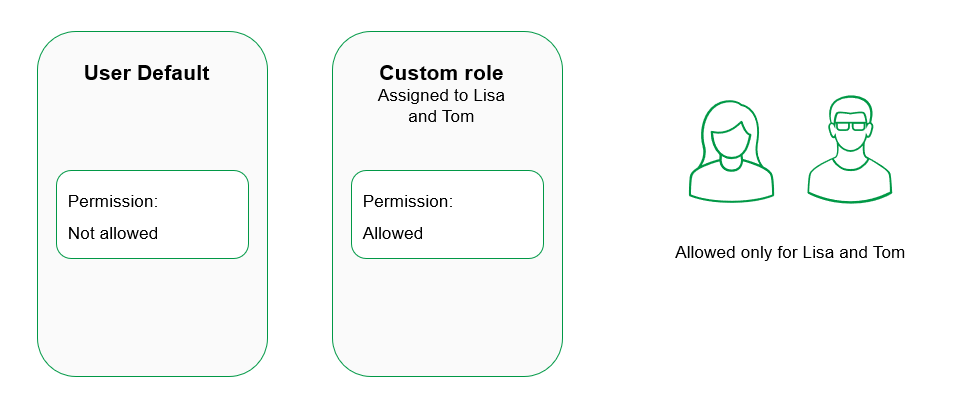
If you wish to restrict the permission only to certain users—say, Lisa and Tom—using a custom role, you must set the permission in the custom role explicitly to "Allowed" and change it to "Not allowed" in the User Default settings.
When the permission is set to "Not allowed" in the User Default, only users assigned the custom role have access.
How security roles interact with the Data Integration subscription
The Data Integration subscription gives you access to the Data Integration home and to security roles specifically designed for data admins and data spaces.
