SAML authorization
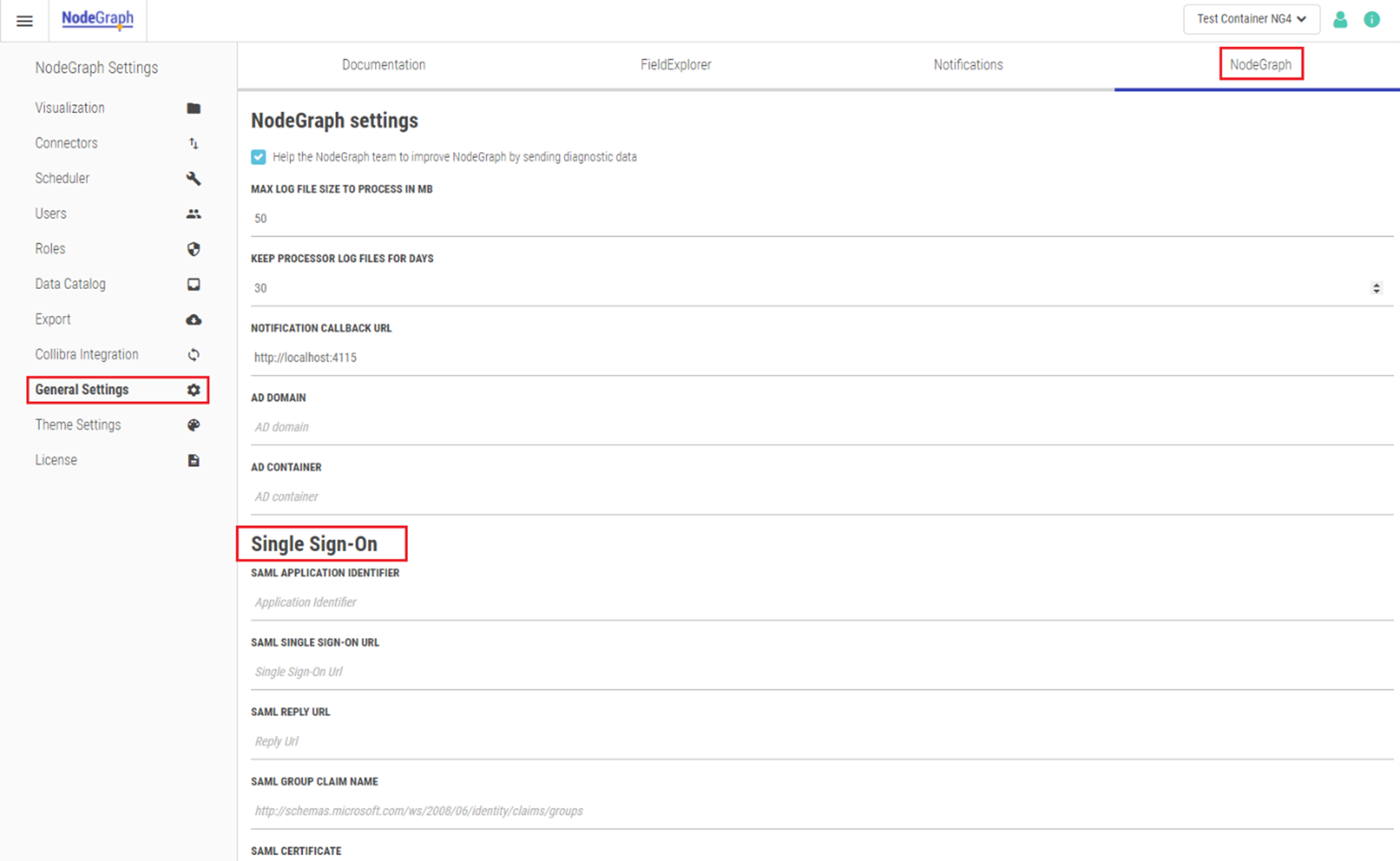
SAML SSO can be enabled by setting authentication mode to SAML. Once SAML is set, further configurations are done through the user interface, under General Settings > NodeGraph > Single Sign-On.
SAML SSO configuration under General Settings.
NodeGraph does NOT resolve any authentication when it comes to SAML Setup. It is purely redirecting your calls to the provider and acts upon the response.
SAML application identifier
The Name defined in your SAML configuration to make the calls with. For all SAML setups, a unique identifier allowed to make these calls need to be set and identical to what you see here.
SAML SSO URL
The SSO URL is the URL endpoint on the provider side. This is your Azure/Okta/PingFederate/etc. provider endpoint. It is NOT the NG machine, but rather something like https://azure.domain.com/saml2.
SAML reply URL
When customizing your SAML endpoint, you must provide an URL on your SAML configuration where the response should be sent. This is done on the SAML side. For NodeGraph that is default http://localhost:4114/saml/samlresponse.
It also must be setup for NodeGraph where such a response should be picked up and compared. This is where SAML will post the reply once the authentication is done. Inspecting the JSON Body of the response informs you of the format expected by your SAML setup and what must be set as Local User on the NG Side.
SAML group claim name
This is the name of the property containing the groups this user belongs to on the Identity Provider side. By pointing to this property (and enabling it in the pass-thru), you can give access on group level instead of user identity. For Azure, they return the ID of the group as GIDs (as opposed to group name). To know what is expected here, you must inspect the body of the Json Response.
SAML certificate
The Exported trust certificate to make the SAML calls with. This is obtained from your SAML provider/configuration. This is not optional.
