Security and governance
A Qlik Talend Data Integration deployment is made up of three key components:
Qlik Talend Data Integration
Cloud storage:
- File stores (e.g. S3)
- data warehouse tables
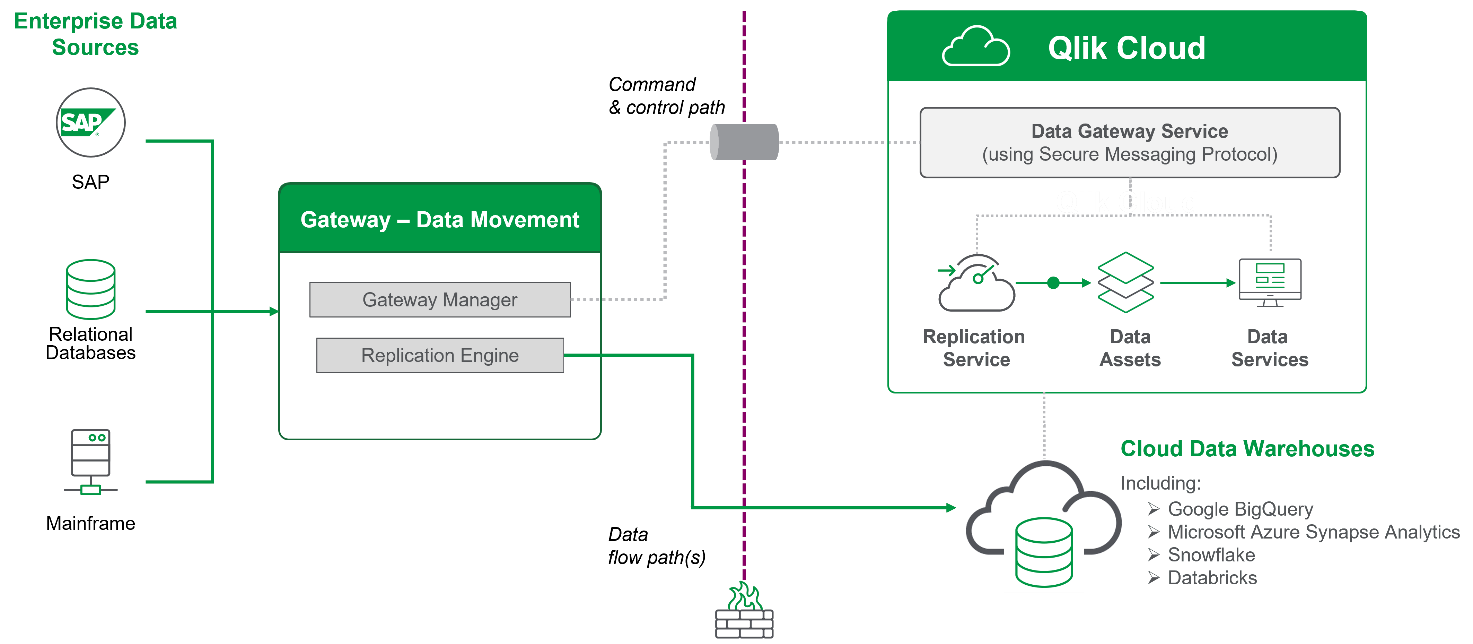
Data Gateway - Data Movement
There are several aspects of how we secure different data delivery strategies, which we will discuss here.
Connection and perimeter security
All the connections from on-premise to the cloud are outbound. This means there is no need to open any port through the corporate firewall, nor to provide a publicly resolvable IP address. The connection is initiated by the data movement gateway and promoted to a web socket secure (WSS) connection, which allows Qlik Cloud to send command and control to initiate the data synchronization. All data in transit is secured by the TLS 1.2 and 1.3 protocol. Command and control plane communication is additionally encrypted with a random channel key which is changed every time the gateway connects to Qlik Cloud.
Data storage
Qlik Talend Data Integration avoids storing data in Qlik Cloud where possible. When it is stored in the tenant, it is encrypted using the tenant's unique encryption keys (optionally using customer managed keys where configured). While Metadata is saved in the tenant's storage, data is only stored in Qlik Cloud if one of the following is true:
Permanent data storage:
- Qlik Cloud is the target platform.
Temporary caching of data:
- Connection to source is direct (i.e. Data Movement gateway is not used).
- Data preview is enabled - this caches a small sample of the tables.
- SaaS connectors are used.
Qlik Cloud as a target
When choosing Qlik Cloud as the target, data from source systems can be stored either in Qlik-managed or customer-managed storage. In these workflows, the only time data is stored in Qlik Cloud is when choosing Qlik Cloud – Qlik-managed storage
as the data platform (target) for a data project. This means that the landed data will reside in a Qlik data space encrypted with the customer's unique encryption keys. Customer must still provide a separate S3 storage area for the landing of the data (staging).
All other targets
If the data platform is any one of the cloud targets, such as Snowflake, Azure Synapse Analytics, Microsoft SQL Server, Databricks, or Google BigQuery, the data will be both staged and landed there, and never in Qlik Cloud.
The Data Movement Gateway's replication engine will directly push source data from on-premise / VPC source systems to the cloud target, only involving Qlik Cloud if the source is a SaaS application (or Qlik Cloud is the target) . The gateway manager will be responsible for metadata and command and control, but never data transfer.
Generative AI
Some optional features of Qlik Talend Data Integration use generative AI. These features are disabled by default and it is up to each customer to decide if using these features meets the customer's policies. When using generative AI features in Qlik Talend Data Integration, a customer's metadata only will be sent to our generative AI shared services which operate within the same region as the customer's tenant. This communication is via a private network and at no time is this exposed to public endpoints. At no time is customer data sent to the generative AI services.
Metadata storage
Metadata about the data source and connections are stored in Qlik Talend Data Integration and are not persisted in the Data Movement Gateway. Metadata required to run a job is transferred securely to the gateway, but is kept in-memory and not persisted to the gateway server.
Data encryption
The Data Movement Gateway communicates with the source and target endpoints (typically databases) using either the vendor-provided client package or via a standard ODBC driver. For this reason, the Data Movement Gateway relies on the source/target endpoint's vendors for the in-transit encryption. While the majority of vendors all support encrypted connections, it is out of scope for this document to cover the specifics of other vendor software.
Databases are assumed to sit on a private high-secure network with limited access from other applications. The Data Movement Gateway requires access to the source databases. Data landing on the client-managed cloud storage can be encrypted using server-side encryption.
Qlik Cloud offers data at rest encrypted with the tenant private key or optionally with the customer's own managed keys. For more information about encryption, see the Qlik Cloud platform evaluation guide.
Service-to-service authentication and authorization
The Data Movement Gateway uses a JWT-based token to communicate with Qlik Cloud. Communication between the Data Movement Gateway and Qlik Cloud is always encrypted with TLS 1.2 or higher.
Client-managed cloud storage (S3 bucket) requires a key and secret and is subject to IAM control. This allows customers to set the read/write permissions for different buckets. See What is IAM? for more details.
User authentication and authorization
Authentication
Authentication of users on the Qlik Cloud platform is handled by the configured identity provider:
Qlik Account — This is the default mechanism and is managed by Qlik. It provides a secure but basic authentication solution for customers, however is not configurable and does not integrate with a customer's existing solutions.
Third party identity provider — Qlik Cloud supports configuring third party identity providers that support the OpenID Connect (OIDC) protocol.
For more information about authentication, see the Qlik Cloud platform evaluation guide.
Authorization
Users of Qlik Talend Data Integration are managed using the same role based access control system as is used for the rest of Qlik Cloud. The available space based roles are described in the following table:
| Data space role | Summary |
|---|---|
| Is owner | Full permissions on the space including the ability to grant others access |
| Can view | Monitor, but not alter the data pipeline |
| Can consume | Consume data from data tasks in the data space |
| Can manage | Manage the space details and members |
| Can operate | View data tasks with basic details and perform actions, such as run, stop, and resume |
| Can edit | View and edit data tasks in this space, as well as create new data assets |
In addition, there are several system-wide data integration roles available:
| System role | Summary |
|---|---|
| Data Admin | Administrator with limited permissions to manage only data spaces |
| Data Product Manager | A user who can create data products |
| Data Space Creator | A user who can create data spaces |
| Data Services Contributor | A user who has access to Data Integration services |
For more information about platform level authentication and authorization, see the Qlik Cloud platform evaluation guide.
