Standards and compliance
Compliance and privacy
When moving workloads to a SaaS platform it is vital to know that data will be secure and that the service provider is following open and audited processes for security controls. Qlik Cloud has been built from a secure-by-design framework as a secure platform. Qlik also works with external parties to meet the applicable industry and Government standards and/or to ensure that best practice controls are in place.
Qlik Cloud government, our dedicated offering for the U.S. Public sector, is covered by a different set of standards as required by the government sector. Details on these are covered here: Qlik Cloud Government Compliance.
For the latest information on Qlik’s external certifications and compliance, see our Trust page.
ISO: the International Organization for Standardization
ISO is an independent international organization committed to creating standards based on best practice. ISO bring together experts to understand and document better and safer ways to operate and publicized these though standards. Organizations can undertake certification to show their adherence to ISO standards.
ISO 27001
Qlik is ISO 27001 certified, meeting the international standards for implementing an information security management system (ISMS). An ISMS is a framework of policies and procedures that includes the legal, physical, and technical controls involved in an organization’s information risk management processes.
ISO 27017:2015
Qlik meets the standards of ISO 27017 an information management security specification for information management systems (ISMS) covering cloud security controls for cloud service providers. ISO 27017 is an extension to the ISO 27001 ISMS framework.
ISO 27018:2019
Qlik meets the standards of ISO 27018, an information management security specification for information management systems (ISMS) covering cloud privacy requirements and security controls for cloud service providers. ISO 27018 is an extension to the ISO 27001 ISMS framework
SOC: The System and Organization Controls framework
The System and Organization Controls (SOC) framework was created by AICPA, the American Institute of Certified Public Accountants. SOC is a standard for controls that protects information. Implementing SOC frameworks involve two phases:
- Implementing and maintaining SOC controls (SOC Compliance)
- External review process to verify and document and organization's compliance (SOC Certification)
SOC 1 Type 2
Qlik Cloud is AICPA SSAE18 SOC 1 Type II compliant. Qlik has successfully completed a SOC 1 Type 2 assessment, which provides an evaluation on the suitability of the design and operating effectiveness of Qlik's internal controls, reporting on an Examination of Controls at a Service Organization Relevant to User Entities’ Internal Control Over Financial Reporting.
SOC 2 Type 2 + HITRUST CSF
Qlik Cloud is SOC 2 Type 2 compliant. SOC 2 is a rigorous examination by an independent accounting firm based on the AICPA Trust Services Principles. It provides an evaluation of the design and operating effectiveness of Qlik’s internal controls.
SOC 3
Building on SOC 2, Qlik has successfully completed a SOC 3 assessment, which is a general use report attesting to Qlik’s compliance to the AICPA Trust Services Principles.
Global and industry specific standards and compliance
Cloud Application Security Assessment (CASA)
CASA has built upon the industry-recognized standards of the OWASP's Application Security Verification Standard (ASVS) to provide a consistent set of requirements to harden security for any application. Qlik has achieved CASA Tier 3 certification.
Cyber Essentials
Qlik has successfully completed the Cyber Essentials Certification, a UK Government-backed, industry-supported certification.
Cyber Essentials Plus
Cyber Essentials Plus is a UK Government-backed, industry-supported certification scheme introduced in the UK to help organizations demonstrate operational security against common cyber-attacks. It is backed by industry, including the Federation of Small Businesses, the Confederation of British Industry and a number of insurance organizations that offer incentives for businesses holding this certification. Qlik has achieved Cyber Essentials Plus accreditation, showing our commitment to mitigate threats within the context of the UK government's "10 steps to Cyber Security".
HIPAA/HITRUST
Qlik supports customers with their HIPAA regulatory requirements via the HITRUST CSF certification. Qlik requires it as mandatory for Customer Managed Keys (enhanced encryption) to be configured and a Business Associate Agreement (BAA) to be signed with Qlik prior to loading personal health information into Qlik Cloud.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a United States federal statute governing the flow of healthcare information and provides federal regulatory standards that outline the lawful use and disclosure of protected health information in the United States.
HITRUST (Health Information Trust) is an independent testing organization. The HITRUST CSF (common security framework) is a framework that an organization can use to meet the legal requirements of HIPAA. HITRUST offers measurable criteria and objectives for applying appropriate administrative, technical, and physical safeguards that are also covered by HIPAA. Qlik has successfully completed a SOC2 Type 2 + HITRUST attestation for HIPAA compliance.
IRAP
IRAP is an assessment process required by Australian Government bodies wishing to use Cloud services. Qlik has been assessed by an independent Information Security Registered Assessors Program (IRAP) assessor against the Australian Government Information Security Manual (ISM) Controls produced by the Australian Signals Directorate (ASD). The assessment examined the security controls of Qlik Cloud and provides assurance that Qlik has met the controls required by the ASD.
TISAX
QlikTech Inc. is a TISAX participant and has completed a TISAX assessment. TISAX was developed by the Association of the German Automotive Industry (VDA) in partnership with an association of European automotive manufacturers, called the European Network Exchange (ENX). TISAX is a registered trademark and governed by ENX Association. The ENX Association governs TISAX on behalf of the German VDA.
UK G-Cloud
Qlik Cloud is an authorized supplier for UK G Cloud v14 on the UK Government's digital marketplace.
General Data Protection Regulation (GDPR) & Data privacy
The General Data Protection Regulation ( (EU) 2016/679, abbreviated GDPR) is a European Union regulation on information privacy. Qlik has built comprehensive internal processes to ensure Qlik’s compliance with applicable privacy (including GDPR) requirements. Qlik is committed to protecting the data of Qlik customers and partners and communicating in an open and transparent manner. Customers may store their personal data in Qlik Cloud, per our online terms. When doing so, Qlik would be classified as a Data Processor in terms of that data under relevant privacy laws, including the GDPR. For more information, see our Privacy page.
Data separation, storage, and transport
Qlik Cloud is a multi-tenant platform. As a multi-tenant platform, it is critical that each customer’s data is separated from the others. Accordingly, each tenant has a uniquely generated set of encryption keys that Qlik manages, or optionally that the customer manages (known as customer managed keys — see the following section). Each tenant's keys are separate from the keys that Qlik uses to secure service-to-service communication. The following encryption is used within the Qlik Cloud platform:
In transit - TLS 1.3 encryption
At rest - AES-256 encryption
Within the platform – Upon authentication with the customer’s designated IDP, uses signed JSON web tokens (JWTs) to ensure integrity, authenticity, and non-repudiation
User access to the tenant is granted by the customer through the identity provider and permissions are controlled via the customer’s administration portal.
Data location
Any customer data that is loaded into the tenant, including any data within backup/recovery and disaster recovery systems, is maintained within the Qlik Cloud services region(s) chosen when creating their tenant. The customer controls whether data is transferred out of region, and none of the data the customer has within the tenant is transferred out unless the customer elects to do so, for example by allowing access to a user in another region. Copies of backups are stored at a secondary location within the same region if available. For details of the backup locations of each see Creating and configuring the tenant
Customer-managed keys
Qlik Cloud provides the ability for customers to use their own master keys from external key management services to encrypt their data that is stored on Qlik Cloud. This capability allows customers to encrypt their per-tenant data with their own key. This capability supports customers who have additional encryption requirements due to regulatory, data privacy, or data sovereignty requirements. Currently, Qlik supports the AWS key management system. Other key management systems will be evaluated in the future.
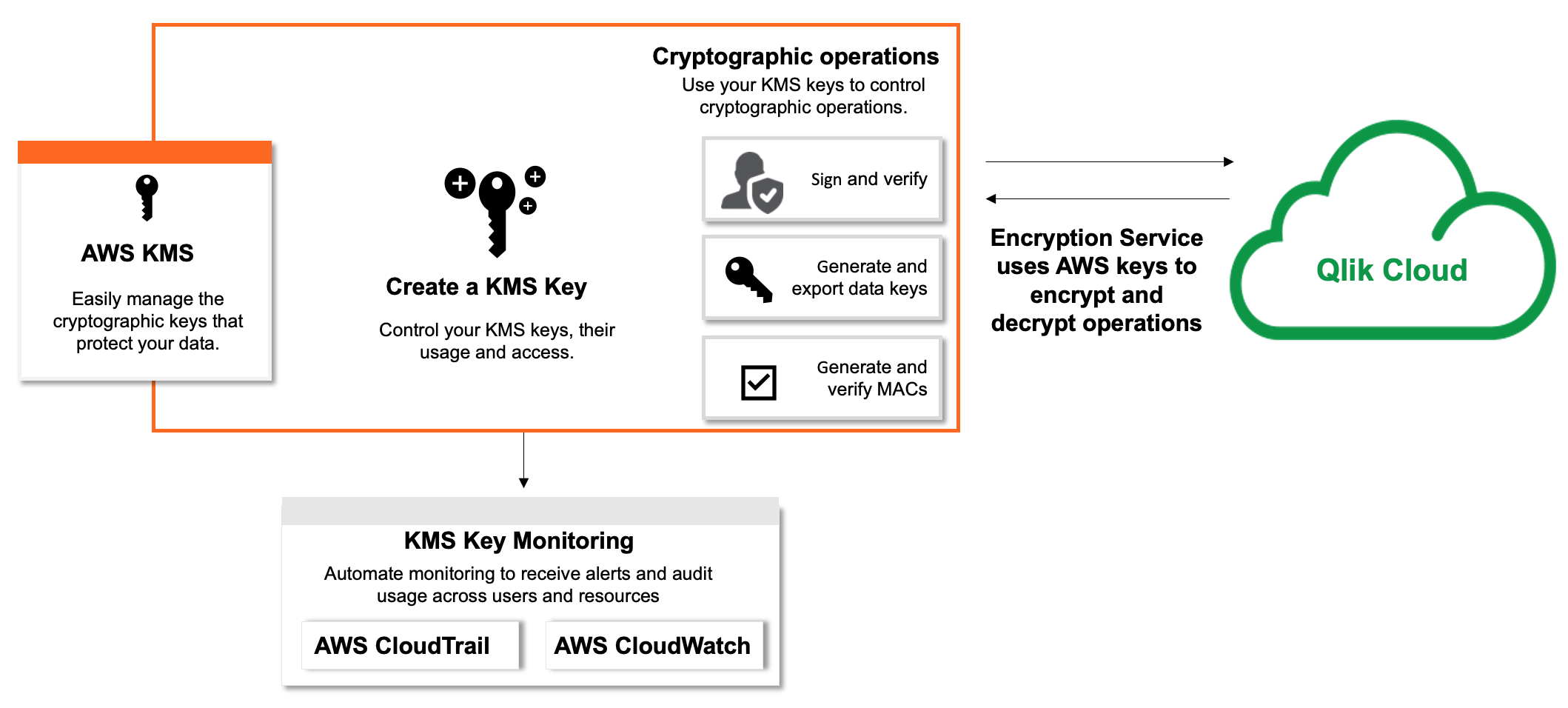
Customer-managed keys provide the ability to move existing Qlik Cloud tenants from Qlik-managed to customer-managed keys, and also to revert from customer-managed keys to Qlik-managed Keys, or to switch between AWS KMS keys. Qlik also supports managing customer-managed keys through Qlik App Automation for both standard and OEM Qlik Cloud tenants. For customers who wish to manage this using their own solution, Qlik provides public APIs for key management.
The Customer Managed Keys feature supports Multi-Region Keys to provide Disaster Recovery in the event of failover of a region. This requires a multi-region key to be used as the customer managed key. The AWS Key management service does not support changing a single region key to a multi-region key, however Qlik Cloud does support switching keys, so this would be required should you wish to migrate to multi-region keys.
Content deletion
"Content” is the customer-provided data and other information within the Qlik Cloud tenant. The creation and removal of content that resides in the tenant is controlled solely by the customer and any content can be deleted by the customer at any time. Backups are removed after a period of time in accordance with Qlik’s internal data retention policies.
Customer-provided data is stored as encrypted QVD or QVF files in the underlying Kubernetes storage solution used by Qlik Cloud. When a customer deletes an app in Qlik Cloud, the service deletes the file on the underlying Kubernetes storage solution. Qlik Cloud relies on the Kubernetes storage solution file system to execute the delete in the underlying block storage.
Qlik leverages our cloud providers for backups to maintain copies of content for 30 days before that content is deleted from the supporting file systems. Qlik Cloud leverages our Platform backups with simple storage remote sync and Amazon Service (S3) to copy content for backup purposes.
Qlik Cloud platform security
Monitored for security 24/7
Qlik Cloud is monitored by Qlik’s Site Reliability Engineering (SRE) team. All security logs are centrally processed by the SRE team, and all incidents are handled in accordance with Qlik’s incident response program.
Security best practices
In order to ensure a strong, secure foundation, Qlik shares security responsibilities with AWS. These cloud computing services are used by Qlik for internal purposes as well as Qlik’s clients for their own cloud deployments. For more information, see the section above on Compliance and privacy.
Qlik Cloud relies on cloud infrastructure for secure physical access, redundant (fault-tolerant) infrastructure, and scalability. Our cloud partner's network design and monitoring mitigate common types of network security issues such as distributed denial-of-service (DDoS), man-in-the- middle (MITM), IP spoofing, port scanning, and packet sniffing.
Qlik’s approach to security builds on our cloud partner's layers of security. Qlik has network and endpoint monitoring controls in place, including intrusion detection and process monitoring. At the web layer, Qlik uses a web application firewall to detect and prevent attacks. Access to Qlik Cloud leverages multi-factor authentication and role-based access control.
Qlik performs regular vulnerability testing both at the network and endpoint level. Vulnerability remediation is incorporated into the continuous deployment methodology in Qlik Cloud. These tests are conducted by an independent third party and include but are not limited to:
OWASP top 10
SANS top 20
Approach to vulnerability management
Qlik’s software development process incorporates a secure-by-design approach to software delivery. A significant contributor to that process is our approach to vulnerability management. Qlik maintains a modern vulnerability management remediation policy that includes:
Leveraging vulnerability severity ratings based on industry standard common vulnerability scoring system (CVSS) to judge the severity of security issues (scale of 1-10 with 10 being most severe)
A policy related to vulnerabilities identified during development and the release of software with known vulnerabilities including remediation windows
A policy related to vulnerabilities identified in Qlik Cloud platform updates including remediation windows
Customer notification policies for vulnerabilities
Third party software security and remediation policy
Tooling and processes covering threat modeling, dynamic and static code scanning, penetration testing, and third party software components
