Setting up HTTPS for the Enterprise Manager console
Industry-standard security practices dictate that web user interface for enterprise products must use secure HTTP (HTTPS). Qlik Enterprise Manager enforces the use of HTTPS and will not work if HTTPS is configured incorrectly.
As Enterprise Manager uses the built-in HTTPS support in Windows, it relies on the proper setup of the Windows machine it runs on to offer HTTPS access. In most organizations, the IT security group is responsible for generating and installing the SSL server certificates required to offer HTTPS. It is strongly recommended that the machine on which Enterprise Manager is installed already has a valid SSL server certificate installed and bound to the default HTTPS port (443).
Checking if an SSL Certificate is installed
To check whether an SSL certificate is installed, you can use the following command:
netsh http show sslcert | findstr /c:":443"
If an SSL certificate is installed, the output should look like this:
netsh http show sslcert | findstr /c:":443 "
IP:port : 192.168.1.13:443
IP:port : 192.168.1.11:443
IP:port : [fe80::285d:599c:4a55:1092%11]:443
IP:port : [fe80::3d0e:fb1c:f6c3:bc52%23]:443
With a valid SSL certificate installed, the Enterprise Manager web user interface will automatically be available for secure access from a web browser using the following URL:
https://<machine-name>/attunityenterprisemanager
Using the self-signed certificate
Due to the way the HTTPS protocol works, there is no way for Enterprise Manager to automatically provide and install a valid SSL server certificate. Still, in the event that no SSL server certificate is installed, Enterprise Manager automatically generates and installs a self-signed SSL server certificate (as a temporary measure). This certificate is generated on the Enterprise Manager machine and cannot be exported or used elsewhere.
It should be noted that browsers do not consider the certificate to be valid because it was not signed by a trusted certificate authority (CA). When connecting with a browser to a server that uses a self-signed certificate, a warning page is shown such as this one in Chrome:
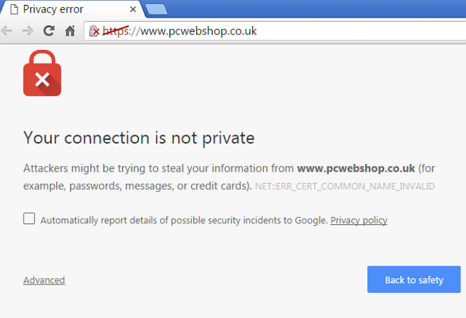
Or this one in Firefox:
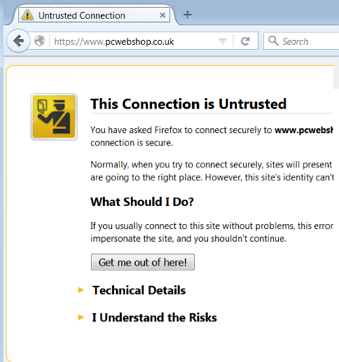
The warning page informs you that the certificate was signed by an unknown certificate authority. All browsers display a similar page when presented with a self-signed certificate. If you know that the self-signed certificate is from a trusted organization, then you can instruct the browser to trust the certificate and allow the connection. Instructions on how to trust the certificate vary between browsers and even between different versions of the same browser. If necessary, refer to the help for your specific browser.
Some corporate security policies prohibit the use of self-signed certificates. In such cases, it is incumbent upon the IT Security department to provide and install the appropriate SSL server certificate (as is the practice with other Windows products such as IIS and SharePoint). If a self-signed certificate was installed and needs to be removed, then the following command can be used:
<product_dir>\bin\AemCtl.exe certificate clean
Note that after the self-signed certificate is deleted, connections to the Enterprise Manager machine will not be possible until a valid server certificate is installed. Should you want to generate a new self-signed certificate (to replace the deleted certificate), simply restart the Enterprise Manager service.
