The following figure shows the authentication flow when using the proxy.
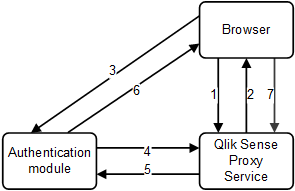
- Access Qlik Sense through the proxy for the first time (that is, browse to the Qlik Sense server).
- When anonymous users are allowed, the client can add a query parameter, “forceAuthentication=yes”, which makes the proxy redirect the browser as described in step 2 instead of just creating and using an anonymous session.
- Proxy sends an Authentication module redirect to the browser.
- Redirect to authentication module.:
- Internal module (implemented as part of the proxy): resides on a different port. The redirect URI contains a query string parameter:
- targetId = <ID for the original URI that the user tries to access>
- External module: the URI is a setting for each virtual proxy. The redirect URI contains two query string parameters:
- targetId (as above)
- proxyRestUri = <the URI where the authentication module can access the REST API>
- Internal module (implemented as part of the proxy): resides on a different port. The redirect URI contains a query string parameter:
- Access the proxy through the Authentication module.
- Authenticate the user and, if successful, create a ticket for the user using the Ticket API. If the targetId from step 3 is included in the ticket request, the original target URI that the user tried to access is included in the ticket response from the proxy.
- Return the ticket.
- Redirect back to the proxy (use the targetUri obtained in step 5) and add a query string parameter:
- X-Qlik-Ticket = <ticket ID from step 5>
- Access the proxy. The ticket is consumed and a connection to the Qlik Sense Engine Service (QES) is established.
Information noteThis first request must use the HTTP GET method, unless you a) already have a valid session, b) use header authentication, or c) if anonymous users are allowed. If this is the case, the request can use any HTTP method.
Information noteWhen creating an external authentication module it is recommended to specify redirect URLs in a configuration file (or similar) in order to avoid an open redirect.
The authentication module differs from the other proxy modules in that it does not expose a REST API. Instead, it makes use of a Ticket API in the proxy.
Tip noteIn some cases, it might make sense for the authentication module to act as a logout module as well.
Two resource types, users and tickets, are used for the authentication flow. Furthermore, the proxy allows the authentication module to post error messages that end up in the proxy logs.
