Inheritance and overrides
Group permission may contradict the permission that a particular user was granted. In this case, the higher permission overrides the lower permission, as illustrated in the following figure:
Group vs. user permissions
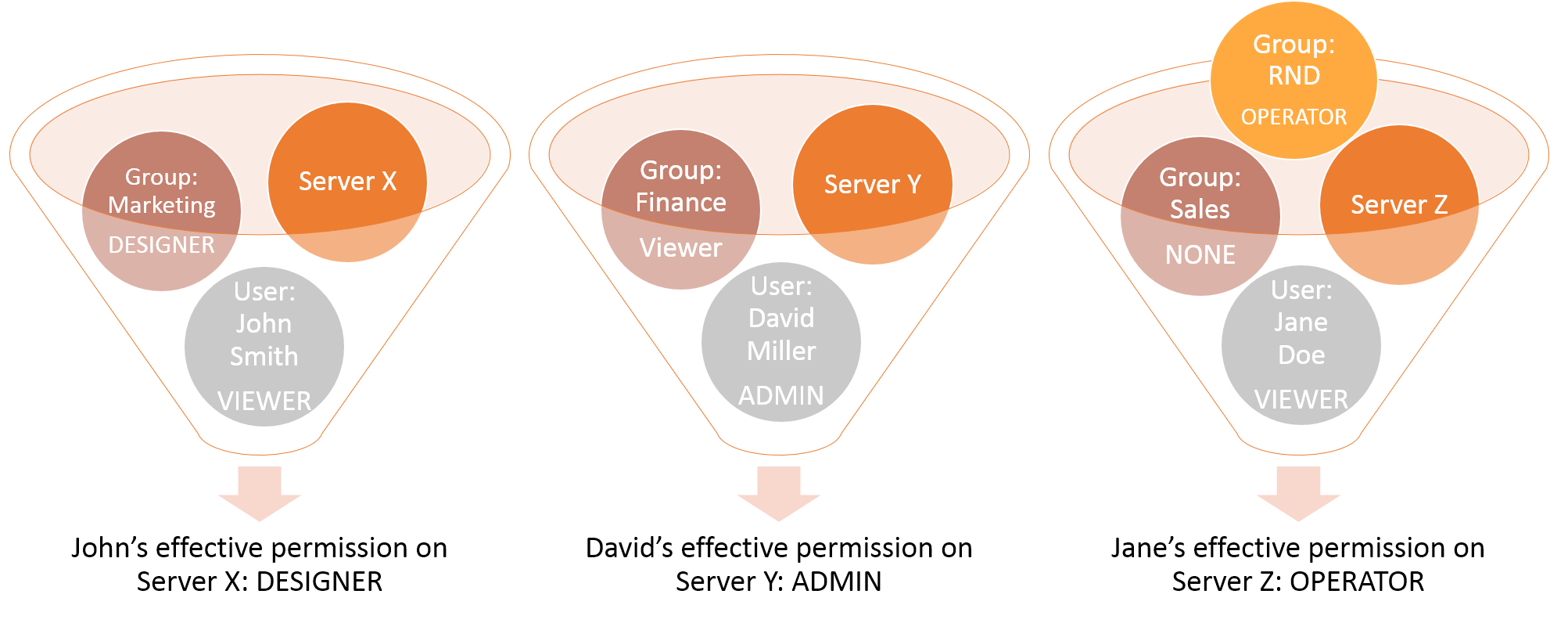
By default, the permission of a user or group object is inherited from the access control list (ACL) of the object's parent. However, a lower or higher permission may override this permission. In this case, the overriding higher permission is the effective permission for the object, stopping inheritance from the parent. As a result, any changes to the parent no longer affect this user or group.
The following figures illustrate these concepts:
Inheritance overriden by higher permission
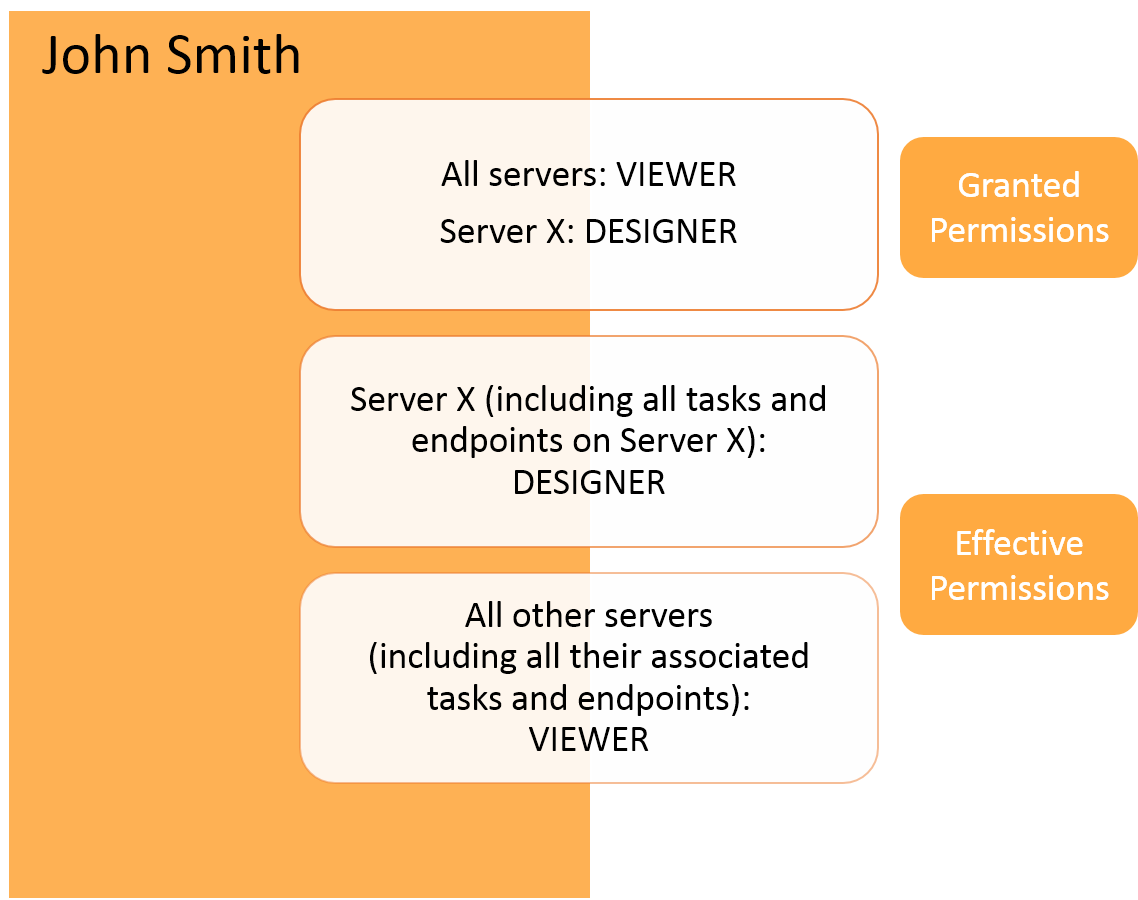
Inheritance overriden by lower permission
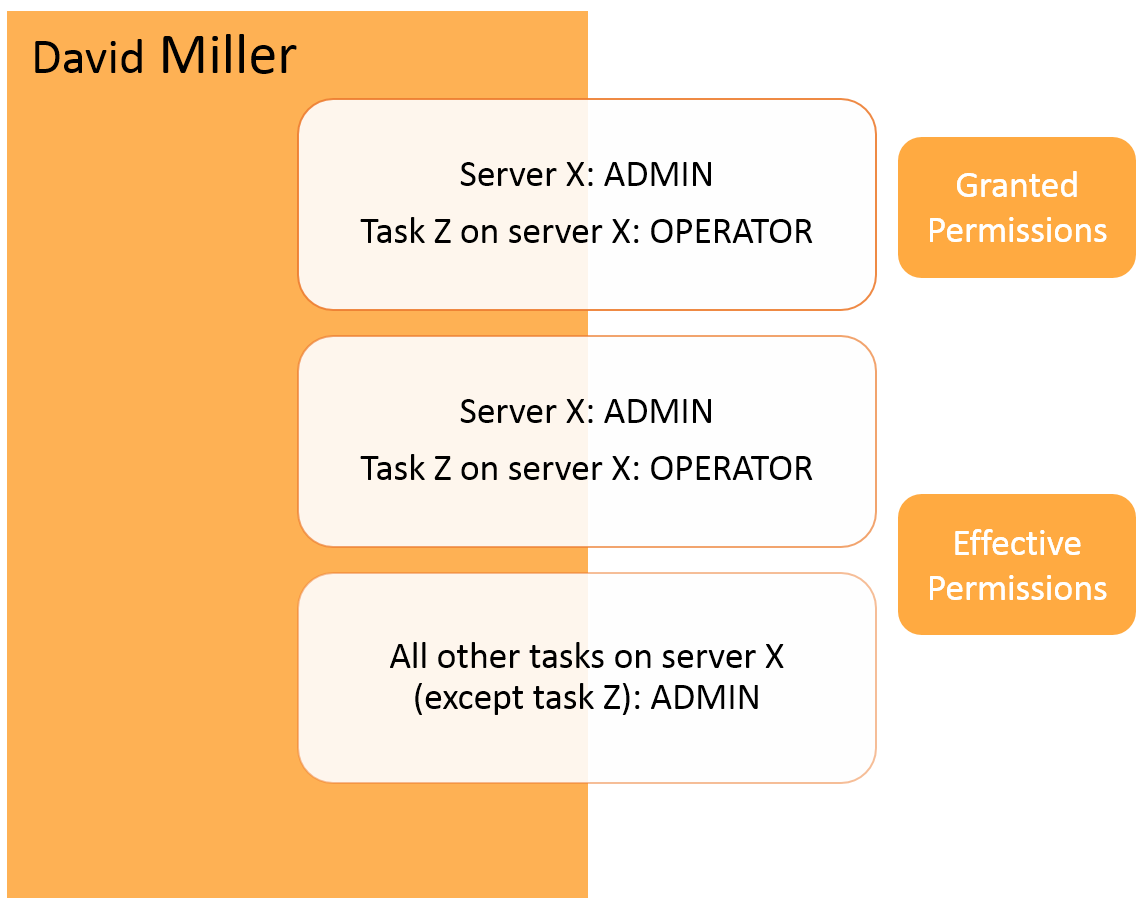
In the User Permissions window, inheritance is indicated by a checkmark in the Inherited column. By default, inheritance is enabled for all users and groups on any level. Changing permissions by using the slider automatically stops inheritance for the selected user or group. Enterprise Manager also lets you disable inheritance by disconnecting the entire authorization level from the parent level. For information on how to do this, see Managing user permissions.
Override exceptions
When a user or group is granted any permission higher than None on an object (except an endpoint), it automatically receives Viewer permission on all parent objects in the hierarchy. However, the Viewer permission granted to the parent objects does not enable the user or group to see items in the hierarchy that they were not permitted to see before they received Viewer permission. For clarification, see the example in the following table:
| - | Granted Permission | Effective Permission |
|---|---|---|
| Server X | None | Viewer |
|
All Tasks on Server X |
None |
Viewer (limited to Task Z) |
| Task Z on Server X | Designer | Designer |
